The Importance of Cybersecurity for Clinics and Healthcare
The importance of Cybersecurity for Clinics and Healthcare
With Healthcare services becoming more and more costly, the aging population, and increases in chronic diseases, the healthcare industry is in great despair. Not to mention the threat of cyber attacks which it is clearly a target for.
In the days leading out of the security breach at LifeLabs which occurred in November 2019, there were many concerns on both sides of the equation. Patients were concerned about their information being leaked to cyber attackers and what that might constitute. In order for LifeLabs to remediate the situation they partnered with Transunion and offered customers 12 months of identity theft insurance.
But this came with hesitation as we should point out, Transunion also had their own security breach sometime between June and July of 2019 where personal data of 37000 Canadians had been compromised, which made customers at LifeLabs concerned about handing over more information to a company that is dealing with more of the same.
Why do we bring this up? Simple, It is the responsibility of the service provider to secure data and limit the access for cyber criminals to attain this information.
Here’s a short list of breaches in the past years (2019) and the final count of customers or records affected.
- LifeLabs: 15million Canadian customers affected.
- Transunion: 37 000 Canadian customers affected.
- Equifax:143 Million customers affected globally - 19000 Canadians
- CapitalOne: 106 million records
- Evite:100 Million records
- DoorDash: 4.9 Million records
- American Medical Collection Agency: 20 million records
- Zoll Medical: 277000 records
- Georgia Tech: 1.3Million
- FEMA: 2.3 million records
Consider this, 60% of SME’s go out of business within 6 months of the attack. According to Herjevac Group, Cybercrime will cost the world $6 Trillion by 2021 - up from $3 Trillion from 2015.
You may have been breached and not know it.
If you’re organization can detect a breach within a 100 days of being attacked, then that puts your organisation 100 days ahead of the game. Alarmingly, a study found that US companies took an average of 206 days to detect a breach which is a slight increase from 201 days from previous years average.
https://www.itgovernanceusa.com/blog/how-long-does-it-take-to-detect-a-cyber-attack
Even more alarming is the fact that senior staff in many organizations seem to think that they won’t be targeted by cyber attacks which in our opinion is an open invitation to get hacked.
Is Your Patient’s Personal Health Information At Risk?
If you’ve been paying any cursory attention to the news then you’ll undoubtedly know that healthcare organizations are becoming targets for cyber criminals. Therefore if you’re reading this then that makes you a forward thinking individual that recognized the importance of safeguarding your patients health information and ultimately keeping your business from hitting the headlines.

How Hackers get in
Some can put the blame of internal mistakes or negligence by healthcare providers which in most cases are common ways for hackers to penetrate.
- Not protecting laptop computers
- Using CC instead of using BCC when emailing patience
- Not overriding former employee login credentials after employment is terminated.
Amongst some of the issues that also create a cyber vulnerabilities are when clinics and Research centers are working alongside 100’s or maybe even thousands of vendors. The problem occurs when a contact information has been compromised by hackers and used to collect information from unsuspecting employees. Most breaches become possible from smaller to medium sized clinics or health centers with attackers posing as staff from other counterparts.
Isn’t cyber security a job of IT?
Most hackers would love nothing more than to collect login information on a senior staff, considering that any information they request under this guise will be handed to them on a silver platter. This also brings up the importance of training staff to be better equipped from these sort of attacks which should be common practice for SMB’s alike.
In any common workplace employees are constantly being evaluated and compensated for productivity. This puts all their attention to completing their tasks, project timelines and deadlines but what about security ?
So the question becomes, how much is the data worth? $500 000? $1Million? More? The responsibility falls on every single person that is part of the organization to be vigilant and assume some responsibility for whom they communicate with, but, without proper guidelines or process, it can leave the organization as a whole in jeopardy of an attack, thus creating more vulnerabilities. Cyber security companies can address all these issues and help SMBs of all sizes create a tailored solution for their needs.
Would you know if your clinical equipment was hacked?
IOT Risks assessment: Many organizations don’t even know how many devices are connected to their environment making their security vulnerable. The growing number of Distributed Denial of Service DDoS attacks launched, utilising IOT devices, clearly outlines the need to increase security. Most of these attacks happened by botnets that we’re mostly made up of hijacked IOT devices. These attacks can cause a major disruption for organization. It’s gotten to the point that the US Government introduced legislation to force vendors with basic security of IOT devices.
What are the challenges ? With Billions of smart devices sharing and communicating data through IOT and a remarkable amount of devices coming online each day, the complex challenge is to determine who governs permission to see and use all this data.
Furthermore, keeping at pace with the growing demand is another challenge on its own. Even with security standards implemented it’s still hard to determine where data from IOT resides where it goes and how to control it.
This wide dispersion of data creates a broad attack surface for cybercriminals.

IOT Solutions:
The internet of healthcare things is growing rapidly and its fueled by some of the following:
- Advancements in Technology
- Growing demand for cost-effective treatment and disease management
- Better accessibility of high-speed internet
- Collaboration of top IT companies with healthcare organizations
- Decreased price of sensor technology
Considering the fact that in today’s hospitals there are nearly 10 to 15 devices per bed, these devices are meant to improve patient care so what would happen if they suddenly got hacked. This can have life and death implications. Although no one died from a pacemaker that was hacked, the possibility of this happening does exist. This extends to many other devices that are being used everyday by many practitioners, doctors, physicians…
How to protect IOT Healthcare devices:
Here is 4 steps to addressing the risks.
-
Perform regular risk assessments to determine the risk profile of all technology in use and to help decide what controls should be implemented.
-
Take advantage of purpose-specific solutions to identify, screen, and secure medical devices.
-
Don't forget the cybersecurity basics. System access should be limited to those who need it, password managers should be used to avoid easy-to-break passwords and vendor-issued software patches should be applied when they’re released. Wi-Fi networks should be encrypted as should portable data stores and hard drives on portable devices. Most importantly, robust network protection should be applied and reviewed often.
-
Use training programs to make sure staff know how to spot threats and what to do when they find them. Use regular brush-up sessions to re-enforce the principles.
Security Information and Event Management (SIEM)
What is SIEM? In Short, it’s software products and services combined to deliver real-time analysis of security alerts generated by application and network hardware. In other words, it’s the equivalent of the “eye in the sky” that you’d find in a Casino.
It’s your way to Monitor, Remediate and continuously hunt for threats.
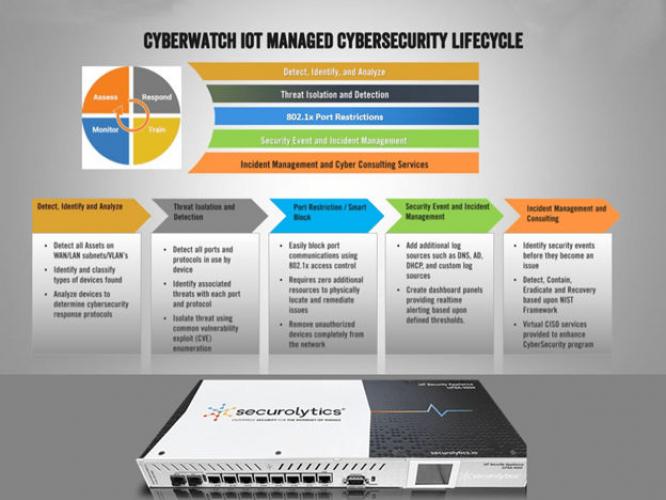
Find out about Secur-Itech's SMB solutions
https://secur-itech.com/cyber
Threat Hunting and Vulnerability Detection services provide an opportunity for organizations to detect, investigate and remediate potential or successful attacks on their systems, networks, and applications. Cyber security companies can you provides the backend infrastructure, implementation services and threat hunting procedures. As always there is not one size fits all solution therefore it’s important that both the organization and the cyber security service provider learn about the ecosystem in order to properly adhere to it’s challenges.
Final note
If you have any questions regarding cyber security or would like to find out how to best protect your organization, please don’t hesitate to contact us Via email or fill a form on our site and it would be a great pleasure to get in contact with you.
Get a Free Consultation, no conditions attached.
Secur-ITech Distributions
Related posts
Endpoints and the Internet of Things Defined by Security
Much consideration should be given to securing endpoints or IOT devices like desktops, laptops, mobile phones and other devices.
Read moreImportance of Cyber Security for Pharmaceutical Organizations
It’s not surprising to know that Pharmaceutical companies are the equivalent of a buffet of information for any cyber criminal to capitalize on.
Read moreGet CyberWatch Security to work for your Small to Medium Size Business
The assumption nowadays for small or medium size business owners, is that they’re in the clear and that cyber criminals are after the big fish. The truth of the matter is that cyber criminals are eager to find ANY weak point.
Read more
